Zero trust – the road towards more effective security – quicklaunch Implementing a zero trust security model at microsoft Microsoft releases zero trust guidance for azure ad
#CyberSecurityTrends' Archives - anteelo
What is zero trust security? principles of the zero trust model
(pdf) design and implementation of the zero trust model in the power
Zero trust deployment center (with videos)Implement zero trust on aws Methodology deployment verify ease iterative palo suggestsZero trust model, architecture & implementation.
Zero trust là gì? tại sao nó lại quan trọng?Adopting zero trust model A practical guide to a zero trust implementation9 shocking facts about network security solutions for small businesses.

Data security model for zero trust implementation
Azure guidance releases paperHow to implement zero trust security model with azure Zero-trust el modelo de ciberseguridad que está cambiando el paradigmaZero trust security explained.
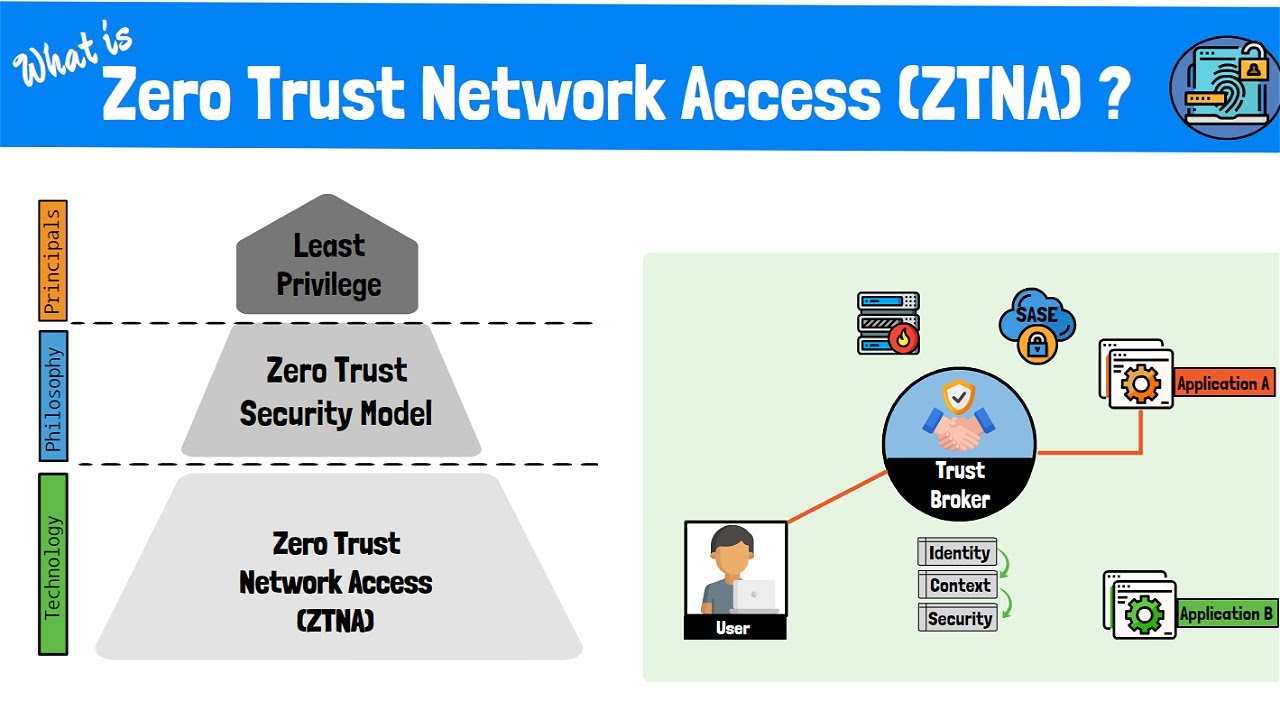
How to implement a zero trust model in your it infrastructureWhat is zero trust security? definition, model, framework and vendors What is zero trust network access (ztna)? the zero trust modelAn overview of the zero trust security model network depot.

Zero trust model defence
Zero security modelZero trust architecture network Microsoft pendekatan cyber akses bersyarat banks cybersecurity keamanan terhadap mengapa menerapkan ilustrasiDesign and implementation of a consensus algorithm to build zero trust.
#cybersecuritytrends' archivesWhat is the zero trust model safeconnect Mengapa bank menerapkan model zero trust, pendekatan modern terhadapImplementing a zero trust security model at microsoft.
Security framework nist crowdstrike principles anywhere cybersecurity
Trust pillar pillars identity implementingWhat is zero trust model? – 7 defence Implement identitiesTrust zero microsoft architecture security model implementing implementation figure diagram services.
Zero trust security modelFakecineaste : zero trust architecture Zero trust security modelZero trust implementation.

Why you need 6 layers of zero-trust control
.
.







